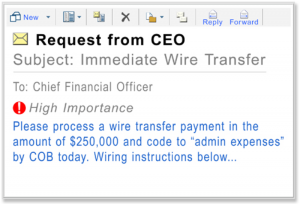
As an attack, the CEO email wire fraud attack couldn’t be simpler. There’s no malware to write and no malicious code or links to implant. It’s a text only email, plain and simple – but it’s the social engineering that makes it work.
Due to its simplicity, these spoofing attacks are one of the fastest growing forms of cyberfraud. According to
the most recent FBI alert, in the last 15 months, the FBI says Business Email Compromise attacks (BECs, for short), often CEO spoofing emails aimed at wire fraud, have increased 270 percent.
[caption id="attachment_6997" align="aligncenter" width="300"]
Credit: FBI[/caption]
During the period from Oct. 2013 to April 4, 2016, the FBI reports losses total a record $2.3 billion, up from $1.2 billion in 2015. In a recent report, the
FBI attributed the increase to organized crime groups.
View the Complete Infographic: The Top Five CEO Email Wire Fraud Attacks

Attackers impersonate a company executive and send a (fake) email message to a finance department employee, instructing the worker to wire funds immediately to a given bank account, usually located abroad. The tone of the emails is urgent.
Because these wire fraud emails bear no telltale traces of malicious payloads, conventional defenses (including widely used SEGs) don’t detect a malicious link or attachment, allowing the email to pass straight through to employees’ inboxes.
Cybercriminals use a variety of methods to identify both the targeted employee and the CEO they wish to impersonate. They may study a CEO’s travel schedule, timing these email attacks to periods when the boss is abroad. Attackers camouflage their true identities when they send these fake emails, pretending to be the CEO, often going to elaborate lengths to hide their true identity. It is not easy for employees to quickly or visually detect that the email is fraudulent.
Unsuspecting employees think they have received a legitimate email from their CEO and are being asked to wire large sums of money quickly to an offshore bank account.
Though obvious in hindsight, these attacks are significant, and victims of email wire fraud are reporting financial losses that have risen from $17 million to $76 million or even as much as $90 million, for a single incident, according to
Mitch Thompson, head of the financial cyber crimes task force in the New York office of the FBI.
Once the attackers have received the funds in their bank account, they quickly change the money into untraceable forms, using common money laundering techniques to hide their tracks. This can mean buying bitcoins or funneling money through casinos.
After the company discovers that the wire fraud was not a legitimate request from the real CEO, the finance employee who wired the funds is often dismissed. The financial losses are reported internally. Investigations to identify the attackers are conducted, officials contacted, and boards informed. Many companies are required to publicly disclose their losses, and the revelations lead to damage to brand reputation.
Eleven Percent of U.S. Companies Attacked
In a recent survey of 200 U.S. companies with 1,000 or more employees conducted by Vanson Bourne (commissioned by Cloudmark), 11 percent of U.S. enterprises surveyed reported that their enterprises had received wire fraud emails attacks.
Overall, the FBI says that since October 2013, the wire fraud email attacks have involved 108 countries and more than 14,000 victim reports.
Interestingly, in the U.S. enterprise survey, two industries in particular reported receiving a far higher percentage of wire fraud emails – healthcare (20 percent) and retail (22 percent).
The Top Five Reported Losses
Cloudmark has been tracking BEC attacks as the email scams increase in number and severity. Here’s a summary of the attacks that have led to the greatest reported losses over the last 15 months:
January 2015
In January of 2015, Xoom Corp., an international money transfer company acquired by PayPal in the summer of 2015, reported that it
had suffered from a $30.8 million loss in the fourth quarter of 2015. Stock for the low cost payments company, which competes with Western Union, dipped 14%, or $31 million, after the loss was announced, but later recovered. The CFO resigned.
Feburary 2015
- Scoular, $17.2 million (US)
Scoular Co., an Omaha based commodities trader (and one of the top privately held companies in the U.S.),
lost $17.2 million in a spear phishing wire fraud scam.
Sidenote: The Financial Times provides an in-depth version of the Scoular attack that can be found
here.
August 2015
- Ubiquiti Networks, $46.7 million (US)
Months later, in August, Ubiquiti Networks, a San Jose based networking technology company, fell victim
to a $46.7 million attack, wiring this sum to a Hong Kong bank account controlled by the attackers.
January 2016
- FACC, $54 million (Austria)
Fraudsters topped all previous records,
making off with $54 million from FACC, an Austrjan aerospace parts manufacturer that designs and supplies parts to Airbus and Boeing.
February 2016
- Crelan Bank, $76 million (Belgium)
The record for the largest loss from a targeted spear phishing wire fraud attack was broken when Crelan Bank in Belgium
reported it lost $76 million.
Reducing the Risk of a Business Email Compromise
Spear phishing is clearly a major and growing problem for businesses, and attacks involving text only wire fraud messages are increasing rapidly. As the losses mount, companies have tried a combination of tactics to catch these attacks. One method is training employees to create a “human firewall,” since technology that effectively eliminates these emails has not been widely available.
While that should be standard operating procedure, it's often not enough. New, emerging technology shows promising results. Using anomaly detection in conjunction with robust, real time threat intelligence, a sophisticated spear phishing security solution can, in fact, detect and reduce the number of these needle-in-a-haystack spear phishing wire fraud attacks - before they reach the inbox.
Fraudsters won't stop chasing the humans, but intelligent spear phishing protection can detect and outsmart attackers. Companies need to use every bit of intelligence and defense available to them to stay one step ahead of the latest attacks.
Since these Business Email Compromise attacks don't require a large amount of expertise and time to create, attackers will continue to barrage employees with fraudulent emails, looking for the companies with weak spear phishing protection.
The best policy is to harness the most effective technology defenses against spear phishing and "hacking the human," by protecting people and companies with both educational resources and intelligent spear phishing technology to prevent these dangerous attacks.
For more information about Cloudmark Trident, our security solution that prevents spear phishing emails from reaching email inboxes, click here. Contact sales about arranging a free trial today.


