Phishing, and particularly spear phishing, may be low tech, but it remains one of the most potent tools in the cyber criminal’s toolbox. In the past it has usually been used for financial crimes, along with some industrial and national espionage, but there is an alarming increase in attacks aimed at more general intelligence gathering. These may have the aim of discrediting the target organization. Enterprises such as think tanks and universities must now consider themselves potential targets for attacks from nation state actors or hactivists, and take appropriate precautions.
Traditional bulk phishing has very often been aimed at stealing money by obtaining access to financial accounts. PayPal was an early target because of the ease of initiating online transfers. The collection of credit card information or online banking credentials is also commonly attempted. We also see phishing for simple email or messaging credentials that can be used to send further spam.
Bulk spam based phishing of this sort continues to be an annoyance, but is less of a problem than it used to be. Good spam filters will stop the vast majority, and many people are aware of the problem and hopefully less likely to give away their account information to a casual spammer. In fact, developers of phishing tools are now trying to sell these tools cheaply for others to exploit, which is probably a sign that they are not as profitable as they used to be. Here’s a PayPal phishing tool (that also attempts to collect credit card and bank account details) available on the web for $20 in bitcoin.
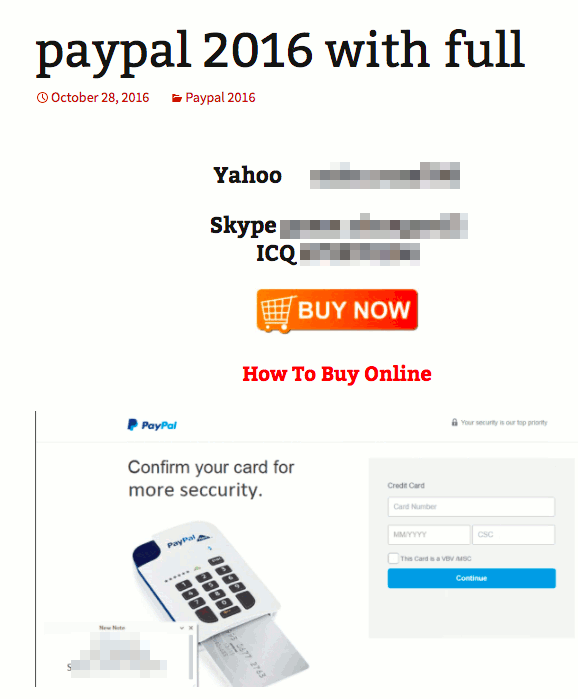
The fact that this and similar tools are being sold rather than used directly by the creators is probably an indication that PayPal phishing is not as profitable as it used to be.
However spear phishing (that is phishing customized to a particular person or organization), continues to be a significant problem, and as
we have reported in the past it is the entry point for a number of the most devastating attacks.
Many spear phishing attacks, especially those aimed at corporate executives, are also financially motivated. One popular attack is an email
apparently from a CEO to a CFO with real names and a realistic looking From: address, which requests a wire transfer of some six or seven figure sum to an offshore account. Another is the attempt to
obtain employee tax information, to be used in subsequent tax fraud. In some cases phishing may just be an attempt to compromise any account on a corporate network in the hope of escalating privileges to collect credit card data from a point of sale system, as happened
in the Target breach.
Spear phishing has also been used for espionage, both industrial and national. Industrial espionage usually seems to be conducted by nation state actors who are
passing information about competitors to corporations with close ties to the national government. There have also been successful attacks against a number of US government departments, including the Whitehouse, the State Department, the Joint Chiefs of Staff, and the Office or Personnel Management. In many of these cases we know that spear phishing created the initial breach. Though there have been a few cases such as ThyssenKrupp and Sony Pictures where attacks based on spear phishing have led to actual damage to plant or systems, in most cases the espionage has been limited to intelligence gathering.
Cyber attackers are discovering that the value of intelligence is not limited to data collected from major corporations or governments. The
hacking and publication of emails from the Democratic National Committee and the Clinton campaign had a significant and perhaps decisive effect on the recent US election. Attribution of cyber attacks is difficult, but several sources point the finger for this breach on a group known as Cozy Bear (aka The Dukes, aka APT27) who are believed to be working for the Russian government.
Cozy Bear’s intelligence gathering has not been limited to the Clinton campaign. Since July 2015
they have been targeting think tanks, universities, and non-governmental organizations with interests in defense, national security, public policy, and international affairs. Most recently they took advantage of the surprise US election result to send out several waves of election related phishing emails, including some purporting to come from the Clinton Foundation. A system administrator at a think tank or university might not think they need the same sort of security as the State Department or the Joint Chiefs of Staff, but the same cybercriminals are targeting them.
The techniques used by Cozy Bear do not rely on sophisticated zero day exploits. Zero days are expensive to buy or locate, and will most likely be discovered and patched if you start using them regularly. Instead, Cozy Bear simply tricks the user into installing malware on their machine. We see very similar techniques used by ransomware and other forms of malware spam: malicious executables in password protected compressed files, documents containing malicious macros, and .lnk files containing PowerShell scripts.
Putting an executable in a password protected compressed file means that virus-scanning software cannot review and block the executable. The password is included in the body of the email message. Encrypting an attachment and then including the password in plain text in the message adds no security whatsoever except protection against virus-scanning, so it should be regarded as a big red flag.
Microsoft Office has long supported a powerful macro language, Visual Basic for Applications, for automating tasks within documents. Unfortunately these tasks can include the installation of malware over the Internet. As a security measure macros are disabled by default on downloaded content, and the user must click on a button to turn them on. Rather than give the button a meaningful label like, “Click This Button To Make The Entire Contents Of Your System Available To Russian Hackers,” it is called, “Enable Content”. Spammers use various forms of social engineering in the documents to trick users into turning on macros. Here’s an example of a malware installer.
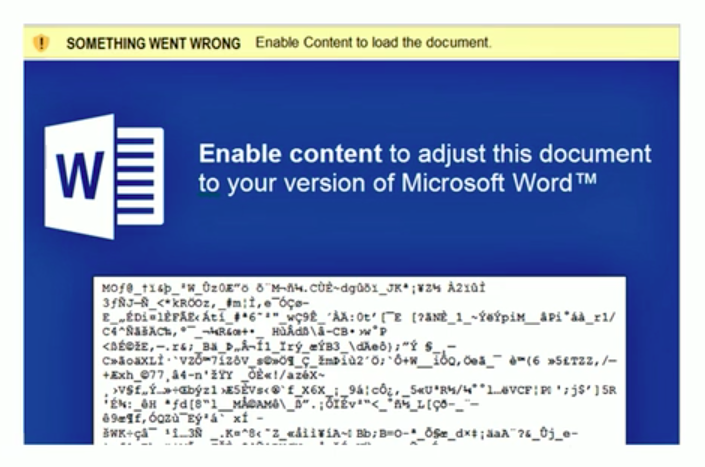
If you do not need them, we would recommend disabling Office macros globally. System administrators can do this for an organization
using a group policy.
PowerShell is a Windows scripting language released in November 2006 that allows the automation of administrative tasks. Yes, this can include the installation of malware over the Internet as well. .lnk files are usually used to contain browser links, but they can also be used to link to a file on your own computer, or even run a PowerShell script encoded in the .lnk file. Thanks, Microsoft. It is possible to
disable PowerShell for an enterprise but this may be problematic as it frequently used for system administration.
All of these attacks only affect Windows machines. If you read your mail on your mobile device you are less likely to be hacked. Sometimes a malicious document will claim that the content is only available on Windows machines, so you should go and read it on one. It’s easy to make a document cross platform, but it is harder to do that for a malware attack, so this is another big red flag.
To conclude, phishing for information or access is as much or more of a problem as phishing for financial data. You may be subject to phishing attacks not only because of who you are, but also because of who you communicate with or do business with. (The Target breach was started by a phishing attack on their HVAC contractor.) Treat all unsolicited email with extreme suspicion, don’t click on links or open attachments, and use secure methods of communication rather than email wherever possible.


