The recent detection of the Onliner spam botnet, which uses 80 million compromised email accounts to send spam to 711 million targets, is shocking in its size but not in the techniques used. Spammers have long used compromised email accounts to send spam. This avoids email filtering based on the source IP address. However, a compromised email account can be used to send more than just generic spam. It can make the spam more realistic by forwarding or replying to genuine emails and adding malicious attachments to them. Here's an example of how this works. On June 2nd a well known company in the food industry sent out an email to their distributors with a large CC list (redacted in the image below).
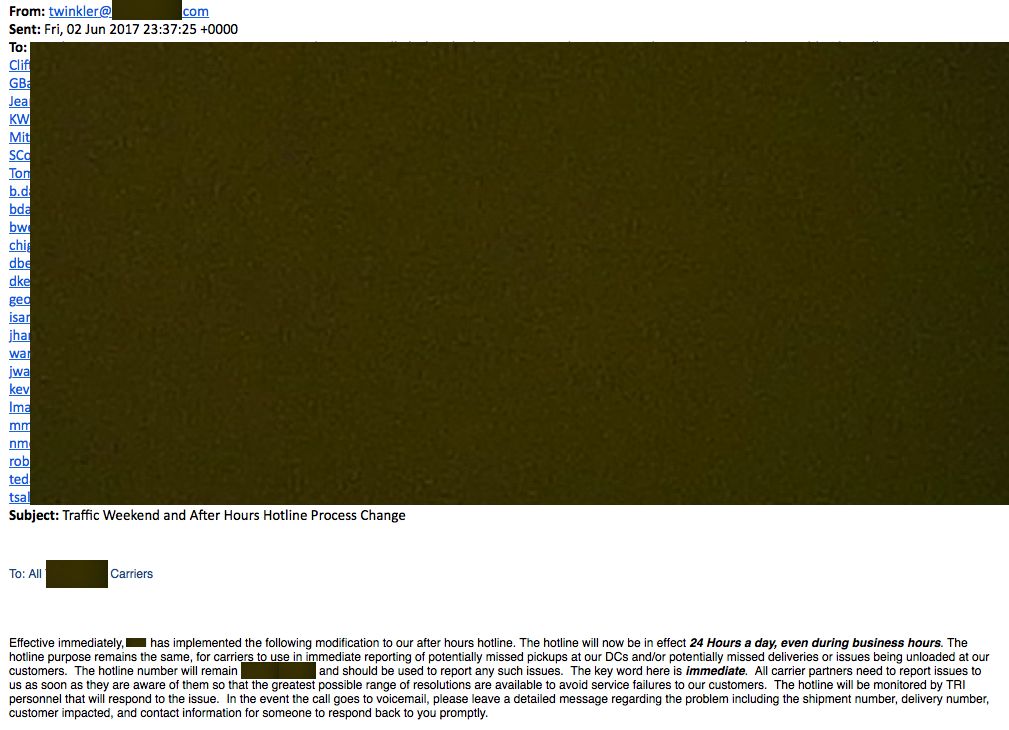
One of the email accounts on the CC list was compromised by a spammer. On August 31st that account replied to another account on the cc list (and probably all of them) quoting the whole of the original message and adding a short note and an attached Word document.

The Word document tries to trick the user into turning on active content so that it can download further malware.
At present only a small fraction of name brand antivirus engines detect the above sample as malicious days after the original samples have been seen in the wild, so you cannot rely on your AV software to protect you against this threat. Cloudmark does a good job of marking these messages as malicious. Depending on local policy this may then result in the attachment being stripped out, or the entire message being sent to the "Spam" folder. In the latter case we do see hundreds of users opening these messages from their spam folder on the assumption that they are genuine. We expect this type of threat to grow as other spammers discover the effectiveness of piggybacking on existing emails. Though the percentage of people who will open the attachment and enable active content is small, the payback for the installation of a single banking trojan can be large. Therefore, criminals do not need a high percentage success rate to make a sizable income. ISPs should have outbound as well as inbound spam filtering and should attempt to detect and remediate compromised accounts. M3AAWG has an excellent best practices document on how to do this: https://www.m3aawg.org/sites/default/files/document/M3AAWG_Compromised_User_ID_BP-2014-08.pdf [PDF] If you are an individual email user, don’t email to large lists of recipient using the “Cc:” field. Instead use an email service provider to send individual messages or use the “Bcc:” function of your email or webmail client instead so you don’t expose the recipients’ email addresses to each other. As always, do not open unsolicited attachments even if they appear to come from a trusted source, and never turn on active content in Office documents you receive via email or other untrustworthy communications channels.
