Wikileaks is currently in the process of
releasing thousands of emails stolen from the account of John Podesta, the Chairman of Hillary Clinton’s election campaign. Two of these contain a forwarded email that has been reported to be the original phishing attack that compromised the account. Let’s take a look at how the Clinton campaign might have detected that this was a phishing attack, and avoided being hacked.
We don’t have the original phishing email, but here’s a screen shot of the forwarded copy.
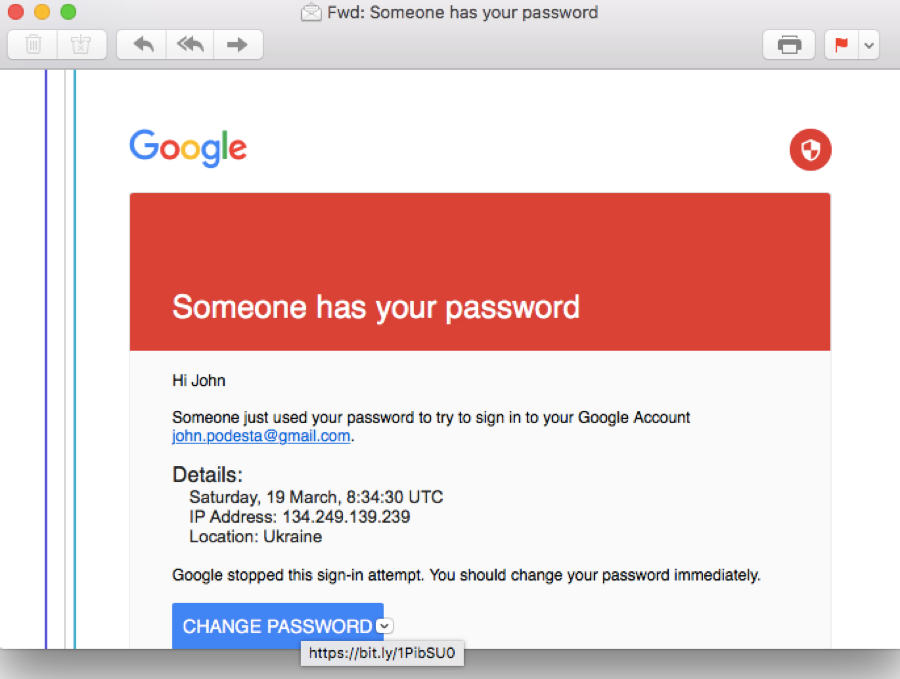
If you hover your mouse over the CHANGE PASSWORD link you see that it goes to a bit.ly link. This in itself is suspicious. Google would not use bit.ly links, as they have their own URL shortener goo.gl. However, it’s possible that Podesta and his staff were using mobile devices with touch screens, which do not allow you to hover over a graphical link to see the URL. The solution to that is simple, and applies to all sorts of devices. Never click on a link in an email telling you to change your password.
If you feel your password should be changed, enter the URL of the account provider manually and change the password there. Frustratingly, as you can see below, one of the staff members who was also taken in by the phishing email still gave exactly this advice, but it appears to have been ignored. (Names redacted by Cloudmark.)
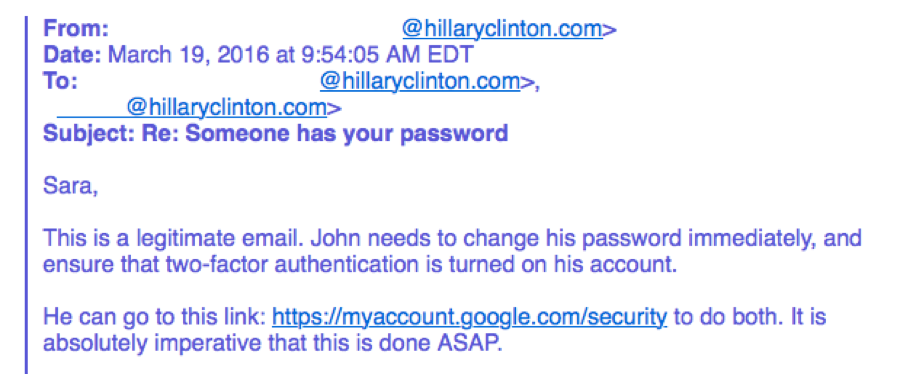
Another staff member offered to help over the phone, but this also did not prevent the compromise. However, even when someone clicked on the bit.ly link, there was still a big hint that there was something amiss. Currently that link is flagged by bit.ly as malicious, but they still show the original URL that the link redirected to.
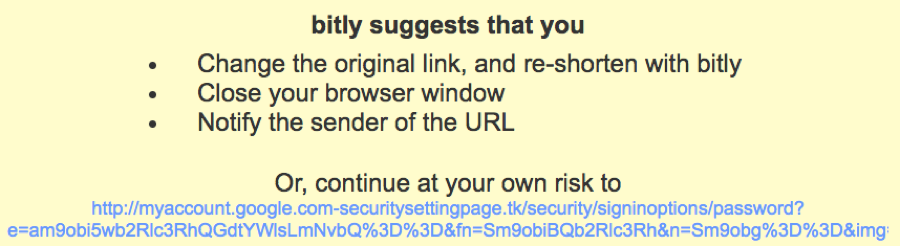
At first glance the URL looks like it is in the google.com domain, but note that the .com is followed by a hyphen rather than a slash. This is a technique frequently used by spammers to disguise a domain. The true domain is com-securitysettingpage [dot] tk.
The .tk top level domain (TLD) technically belongs to the island of Tokelau but it is administered by a company in the Netherlands that provides free domain registration. A huge number of .tk domains have been registered, but almost all of them are used for spam and phishing. Cloudmark’s spam filters will block the vast majority of emails containing malicious .tk URLs. However, it is more difficult to block a URL shortener link that redirects to a .tk domain, especially if it is only used once in a customized phishing attack.
It would be nice if the URL shortener companies would take a more proactive approach to known trouble spots such as the .tk TLD, and prevent accounts from setting up large numbers of links to these, or add a warning automatically to any links that do redirect there. In the mean time, here are some tips so that you don’t get phished.
- Never click on a link in an email telling you to change your password. This is true anywhere, but especially true on mobile devices where you can’t hover over a link to see the true URL.
- If you feel your password should be changed, enter the URL of the account provider manually and change the password there.
- Don’t trust messages in the headers or body of an email saying it has been verified by security software. These are easy to forge.
- Don’t use the same password on multiple accounts. Use a password manager, or use a password modified in some way for each account. For instance, add the first, fourth, and second characters of the domain name to your favorite string of random characters.
- Always keep an eye on the domain that you are visiting in your browser, and be on the lookout for disguised domains using a hyphen after a .com. If you hit one of those close your browser window.
- To the Clinton staff's point: ensure that two-factor authentication is turned on.
- Finally, don’t put anything in an email that you don’t want to see published by Wikileaks. Even if you have perfect security, the person you are writing to might not.



