
Cloudmark’s Security Threat Report for Q2 of 2016 is now available.
This quarter we cover:
- The plummeted distribution volumes of the Locky Ransomware family
- Country report: Bangladesh and Vietnam
- How suing spammers can be successful, a profile on SF-based lawyer Dan Balsam
- Mobile messaging in the U.S. and the differences between carriers and NUVOs
The
full report can be found here and major highlights are below.
Locky & Dridex Distribution Goes Offline
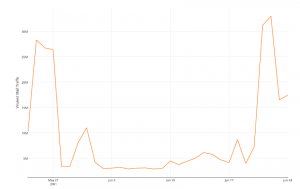
Cloudmark continued to keep an eye on the Locky Ransomware family in Q2 and like several others, we publicly noted that Locky and Dridex-style spam campaigns completely dried up. Their distribution volumes plummeted between May 21 and June 21, 2016 – going from an average of 27 million messages per day to 3.4 million messages per day at the beginning of June. But starting June 21, Cloudmark saw Locky return with its characteristic Jscript inside a zip archive payload.
The actors behind these attacks continued to innovate and shortly after the end of Q2, they replaced JavaScript with obfuscated Windows Script Files (.wsf), still contained in a zip archive. As discussed in the previous 2016 Q1 threat report, Windows Script Files (.wsf) allow mixing of Jscript, VBScript, and other scripting languages within a single XML formatted file. By using this file format, the criminals can repackage their existing JScript code in a .wsf container. During the Locky/Dridex downtime, many similar campaigns stepped up to fill the void.
Virulent Mail Traffic
 Country Report 2016 Q2: Bangladesh and Vietnam
Country Report 2016 Q2: Bangladesh and Vietnam
We examined the spam profiles to Bangladesh and Vietnam – both developing countries have recently come into the security spotlight because of their involvement in bank heists exploiting the SWIFT payment network. Based on our data, Vietnamese and Bangladeshi spammers primarily target Western nations and Vietnamese IPs were the third most prolific Locky senders.
Relative Volume of Spam Sent from Each Country, 2016 Q1-Q2
 NUVOs and U.S. Mobile Spam
NUVOs and U.S. Mobile Spam
In the world of mobile wireless communications, there are two main classes of provider. The first class consists of those operators who own their wireless infrastructure and are typically referred to as Mobile Network Operators (MNOs). In the second class, its operators who don’t own their infrastructure, but instead lease services from one or more MNOs to then resell. Those who contract with only a single MNO are known as a Mobile Virtual Network Operator (MVNOs), while virtual operators who lease services from multiple MNOs are known as Network Unaffiliated Virtual Operators (NUVOs). We examined the messages that were blocked and allowed with members of CTIA. We discovered that NUVOs sends only 9% of legitimate messages and are responsible for 37% of all blocked messages.
Gamesmanship, Laziness and Lies, Oh My!
Finally, we sat down to speak with a man who hates spam, who decided the ‘delete’ button was no longer satisfying. San Francisco based lawyer, Dan Balsam, has turned fighting spam into a unique career. He has been fighting spam for 14 years and has¬ no plans of stopping – especially since he’s won over $2 million in court judgments and settlements against companies accused of sending spam and now represents dozens of clients in superior court.
Interested in hearing more?
Register for our webinar next Wednesday, August 16, at 8:30 am PT or 4:00 pm PT. Leading security experts will reveal more highlights from our Q2 Threat Report and also share practical ways to secure your organization from today’s intelligent threats.
To read more on each of these topics, the
full report is available here.



