Cloudmark’s Threat Report for 2015 Q2 covers the latest in the cyber threat landscape. There are articles on
- Ransomware targeting small businesses
- Using DNS to detect malware infections
- A highly successful FTC action against diet pill spammers
- The abuse of new top level domains like .ninja and .science
- The problems caused by URL shorteners like bit.ly and t.co
- Trends in email to SMS spam
- The spam situation in the United Kingdom
You can
download the full report or read the highlights below.
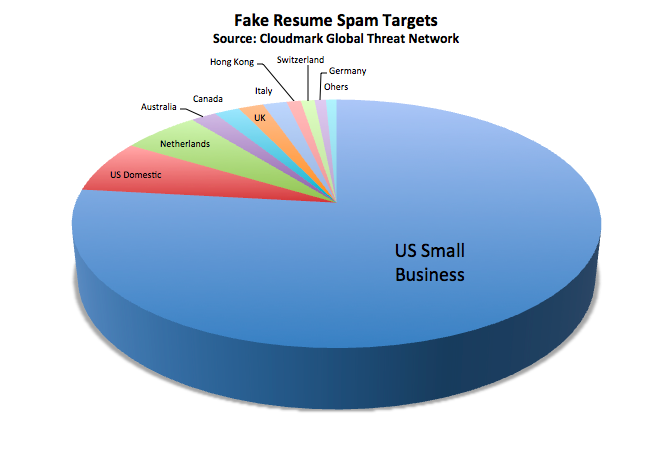
Ransomware (that is, malware that encrypts the files on your hard disk and demands a ransom to restore them) is an increasing threat to all computers. For the Cryptowall ransomware alone the FBI's Internet Crime Complaint Center received 992 complaints between April 2014 and June 2015 with total estimated losses of $18 million. However, it's a particular threat to small businesses, who may have mission critical data on a single computer without adequate backup. Small business are also the main job creators. With 74% of all the new jobs in the US since the end of the last recession created in companies with less than 500 employees, many of them may be looking to hire new staff. A recent spam attack that was specifically targeted at small businesses used fake resumes to try to trick owners into installing ransomware on their computers. Though largely targeted at the US, Cloudmark detected this attack directed at users in fourteen countries on five continents.
While much of the attention in the computer security is directed to the latest zero-day vulnerability or data breach, older forms of malware remain a problem. Cloudmark analyzed DNS data for a major ISP and found traffic from users on their network to command and control servers from malware that is well documented and dates back to 2013. Old malware can be just as damaging as the latest threats if it is not detected and remediated. DNS monitoring provides a useful tool for detection of both old and new malware threats.
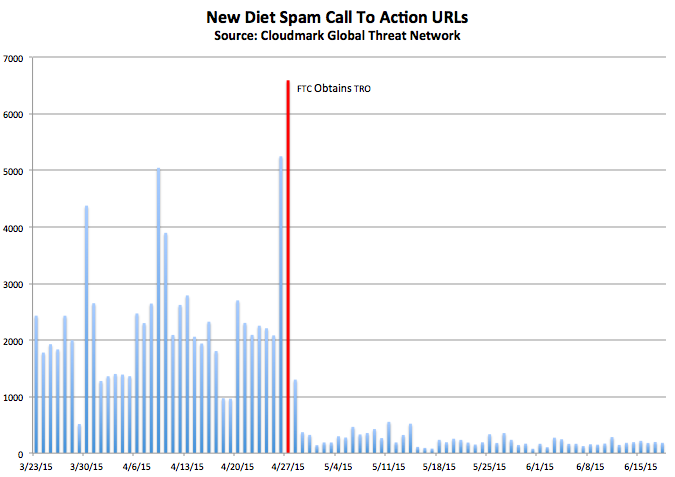
In April, the FTC filed suit against Sale Slash, LLC, a Southern California corporation,

alleging they were responsible for the sale of diet pills using spam marketing, and a variety of fraudulent claims including the use of Oprah Winfrey's name and image. According to the FTC's court filings Sale Slash paid over ten million dollars to one of the spammers promoting their products, identified only by an email address and an offshore bank account in Curacao. Since then Cloudmark had seen a 79% reduction in diet pill spam, and a 90% reduction in new diet pill URLs found in spam, so the FTC's action appears to have been extremely effective.
Recently a number of new top level domains (TLDs) like .ninja, .science, and .rocks have become available. Cloudmark research shows that the cheaper the domain registration, the more likely it is to be abused by spammers, with free TLDs being almost entirely used for spam.
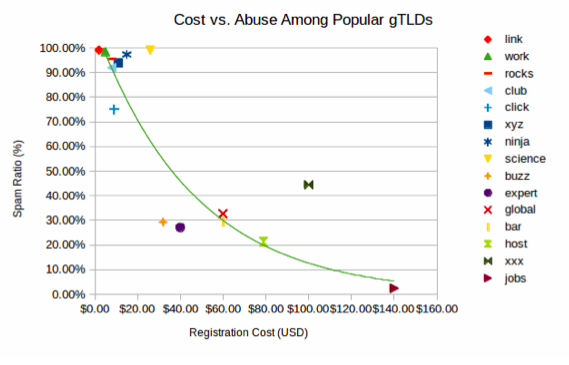
Two outliers for this rule are .science which is attractive to spammers because of it sounds reputable and .xxx which is attractive to spammers because it sounds disreputable.
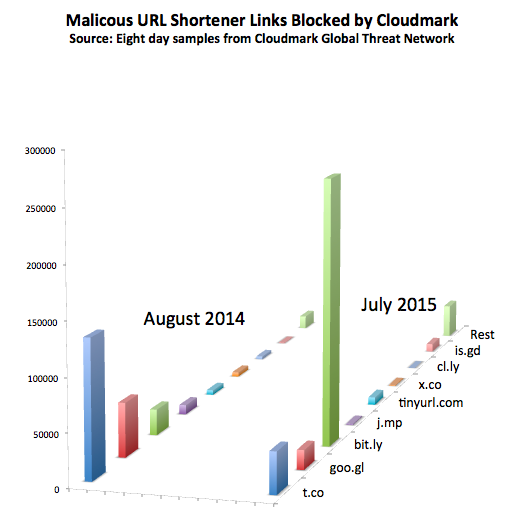
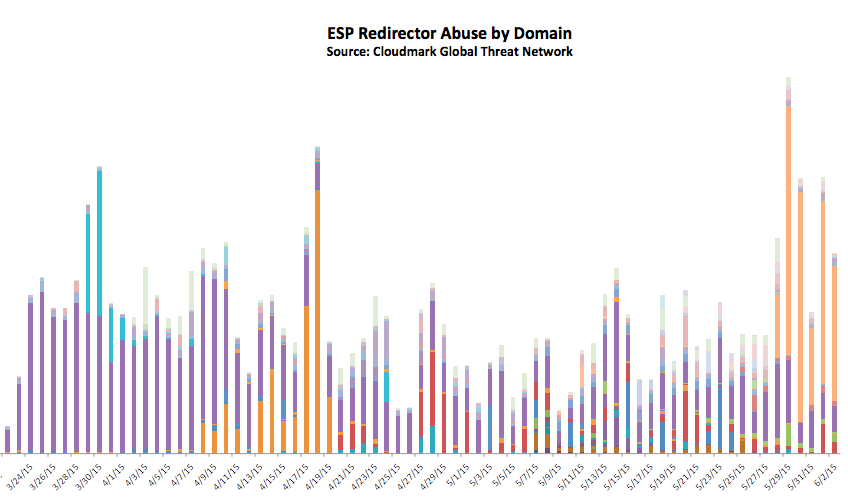
If spammers always used the same call to action URL in their emails, that would be easy to filter. To try to get their spam delivered they need huge numbers of different URLs, though these may redirect to the same few landing pages. We took a look at two techniques that spammers are using to generate redirectors: URL shorteners like bit.ly and t.co, and click tracking services offered by emails service providers (ESPs). In both cases we found that spammers will go where the security is weakest, and will move to a different provider should their current target improve security. A year ago Twitter's t.co URL shortener was a major target for spammers, but as they tightened up their security the spammers switched to using bit.ly.
ESPs provide redirector links for their legitimate customers so that they can track activity from specific mailings. However, spammers have found that they can also use ESP redirector links while sending their spam through other channels. Once again we have seen them switch between multiple ESPs as one or another improves their security. Each color in the chart below represents a different ESP.
The US Department of Justice just announced the successful take down of the Darknode cybercrime forum, and the indictment of a number of alleged criminals. Three of those, Naveed Ahmed, Phillip R. Fleitz, and Dewayne Watts are accused of "...participating in a sophisticated scheme to maintain a spam botnet that utilized bulletproof servers in China to exploit vulnerable routers in third world countries, and that sent millions of electronic mail messages designed to defeat the spam filters of cellular phone providers." Most phone carriers provide free gateways that will take an incoming email message and forward it to a phone as an SMS message. Since it is easier and cheaper to send spam emails than spam SMS messages, these gateways have always been targets for spammers, and it seems that this is what these three are alleged to have have been attempting to exploit. Cloudmark provides spam filtering services for several phone carriers, and we took a look at the sort of spam we are blocking. Currently we are seeing various phishing attacks, including one aimed at people who list items for sale on Craigslist, and also marketing for dubious adult services.
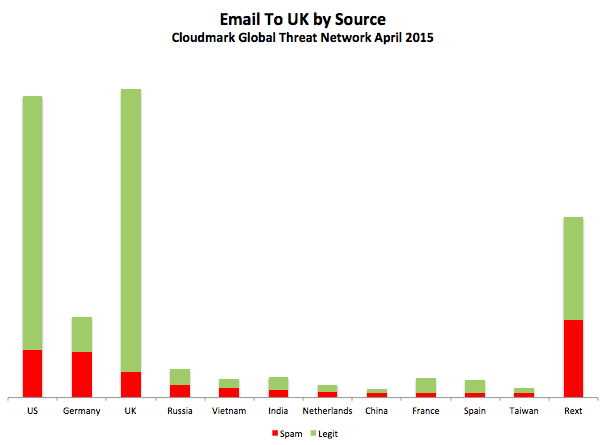
Finally, we took a look that the spam situation in the United Kingdom. Generally the both inbound and outbound spam are at reasonable levels, but we found that in both cases a few rogue ISPs are significantly skewing the statistics for the worse. We found the 14% of the spam originating in the UK could be traced to a single Scottish ISP, Iomart, and the high level of spam from Germany to the UK was due in large part to just three networks.
 Cloudmark’s 2015 Q2 Global Threat Report
Cloudmark’s 2015 Q2 Global Threat Report







