Dyn, a major DNS provider, is currently undergoing a major DDoS attack, which is making it difficult to access a number of websites including Github, Reddit, and Twitter.
Since this attack is targeting the sites’ DNS provider rather than the actual sites themselves, the web servers for those sites are still fully functional. Taking down the DNS server makes it so that browsers are unable that convert the domain names (such as twitter.com) into numeric IP addresses where the web servers reside. Since DNS is a distributed system, this is not even affecting all parts of the world. The attacked started on Dyn’s US East Coast servers, and after a break is now hitting the West Coast as well.
[caption id="attachment_7219" align="aligncenter" width="600"]
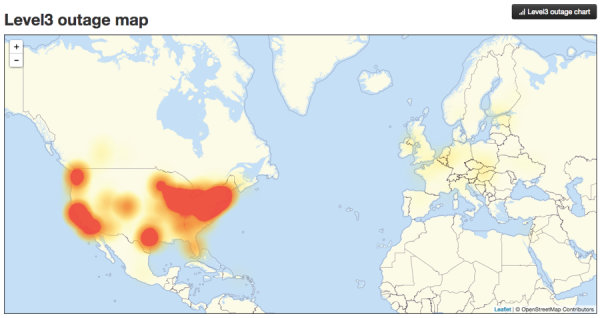
Map as of noon Pacific Time Oct 21. For the current Level3 outage map
see here.[/caption]
We are not certain who is behind this attack, or what means are being used. However, recent large scale DDoS attacks such at the one on Brian Krebs’ website have used a botnet of Internet of things devices that are generally far less secure than most computers, phones, and tablets. Since a researcher from Dyn worked with Brian Krebs on a recent investigation of DDoS attacks, it is possible that the same actors are behind both
the Krebs’ attack and this one.
In the mean time what can you do if you desperately need access to Github or Twitter? Remember that DNS is a distributed system, so you may be able to temporarily
switch to a different provider where DNS is still working. Web sites that cannot be reached through your home or corporate network may still be available on your mobile device, and using the mobile device as a hotspot may give you access on other computers.
Failing that, the attack is currently hitting the US a lot more intensely than Europe, though there is some impact there. Using a VPN to a European location may well let you access that all important Twitter feed that you cannot access from the US. VPN providers that would allow you to do this include:
Of course, this is only a temporary measure until this particular attack is mitigated. I believe it’s quite likely that the perpetrators of this attack will be brought to justice. However, even if they are the wheels of justice can grind awfully slowly. One of the first blog posts I ever wrote for Cloudmark over four years ago was about a data breach at Linkedin, and the hacker alleged to be responsible for that was just arrested a few days ago.
Even if the responsible parties are arrested next month, the techniques they used are widely known, and the skill set required to duplicate this attack is not that great, so we can expect to see similar attacks in the future. In particular, with the US election day coming up in a couple of weeks I think it is quite likely that political zealots on one side or the other my attempt to disrupt get-out-the-vote efforts of the other side.
Long term we have to make sure that IoT devices cannot be hacked by any script kiddie with a list of default passwords. Since industry seems incapable of doing this themselves, we need regulators in the EU and US to set minimum standards for Internet devices, including a unique password for admin access to each device (printed on the device so you can’t lose it), and the ability for the manufacturer to push out cryptographically signed firmware updates to patch vulnerabilities as the are discovered.
Updates and other commentary:
Soghoian's point is a good one. In the US we would need legislation passed to allow federal regulators to set standards for the IoT. The last time an attempt was made to do this the tech industry lobbied against it and it failed. Perhaps after this attack they will not be so determined to avoid regulation.
Mirai was used to attack Kreb's website, but as the code has been been published we can't say with absolute certainty that the same actors are responsible.

