Business Email Compromise (BEC) was the cause of over $263 million in losses during 2015 alone according according to the Internet Crime Complaint Center (IC3). The recently published
2015 IC3 Annual Report lists Business Email Compromise as the single most expensive form of loss, by a wide margin, reported to the IC3 and FBI during 2015. BEC attacks dwarfed every other category in the report. The second highest category of internet crime, Confidence Fraud/Romance, was responsible for only $203 M in losses, stealing $43 million less than BEC attacks.
The IC3 defines BEC cases as:
"a sophisticated scam targeting businesses ... carried out by compromising legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds."
Dating back originally to 2010 according to the IC3, scammers originally honed in on businesses that commonly did business in Asian markets so that wire transfers to foreign accounts, often in Asian countries, were less suspicious. These attacks evolved around 2013 when scammers started impersonating and supposedly hacking the emails of company CEOs and CFOs. Requests to wire funds abroad under the guise of a business transaction were given more credibility when coming from a CEO or CFO. The IC3 also claims that this past year scammers have also begun to pose as lawyers and law firms doling out instructions for urgent wire transfers.
What's even more shocking is the efficacy of these attacks. While the total loss in raw dollars is far and away number one, the number of victims comes in at only 17th. A quick glance might take this as meaning that BEC is less significant, but to the contrary, this highlights just how incredibly effective a single compromise can be. When we compared the total amount of loss to the number of victims, we see that these businesses lost an average of $31 thousand. For comparison Confidence Fraud/Romance 'only' saw a loss of $16 thousand per reported victim. Interesting, the highest return per victim were investment driven scams such as the binary option scams discussed [in several of our recent posts.]
However, the IC3 only reports those incidents which are filed as complaints by the public with the organization. The FBI, receiving IC3 reports and other criminal cases of internet crime, has reported even greater loses due to Business Email Compromise. The FBI
reported last year that Business Email Compromise caused more than $740 million in losses during the 23-month period of October 2013 through August 2015. Early this year, the
FBI then reported that from October 2013 to February 2016 they have seen more than $2.3 billion in losses due to BEC. Extrapolating, we can estimate that the FBI has likely seen $1.5 billion in losses due to BEC during the 6 months between August 2015 to February 2016. This would mean the FBI handled almost twice the amount of monetary loss due to BEC in 6 months than the previous 2 years combined -- a dramatic increase to say the least.
The amounts stolen in individual attacks is also rising. In a
previous post, we detailed a recent list of the largest reported losses associated with Business Email Compromises. The list illustrates the ever-increasing amounts that scammers are able to squeeze out of victims.
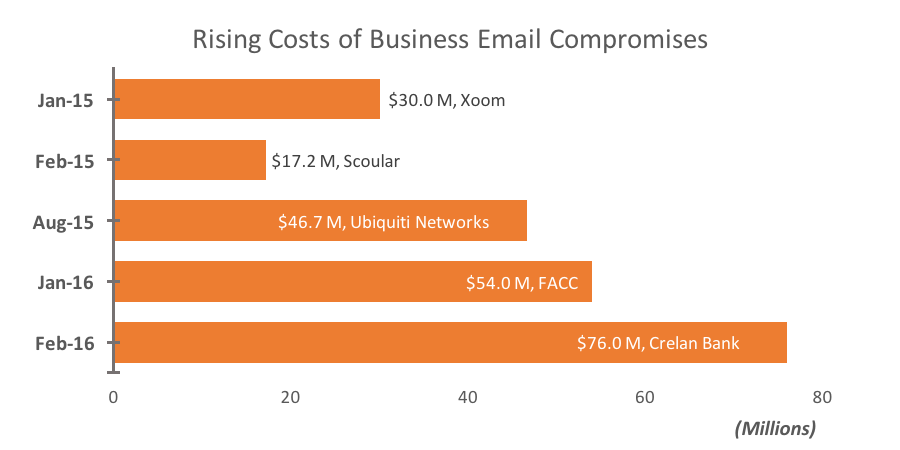
The severity of these attacks are not going unnoticed either. Just last week, FACC (number 4 of the list above) board fired both the CFO and CEO after a 17 percent drop in share price and a net loss of €23 million for the year due to the compromise. In a similar vein, an unnamed employee
was fired from their position at Alpha Payroll Services earlier this year for falling victim to a similar BEC ploy that ended in the theft of the company's W-2 tax records for all employees.
Cloudmark has also been observing and tracking various forms of BEC attacks. Over the past year, we've seen increases in number and severity that resonant with the FBI's and IC3's reporting. Quite frequently we'll see these types of urgent but broad requests come across seemingly from the CEO:
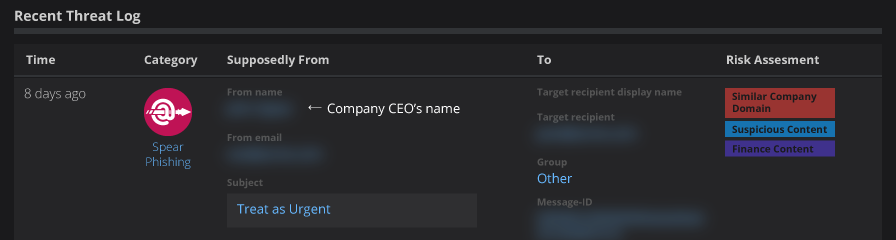
These messages typically use spoofed from addresses to impersonate C-level staff requesting wire transfers. In our recent
Quarterly Security Threat Report we cover a bit more in-depth how such a technique is used. Replying to these requests begins a series follow-up emails asking for the recipient to then wire funds to a provided account overseas under the pretense of being for an on-going deal with the company.


