In a recent blog post, we explored the key differences between phishing and smishing. Unlike email, which can be sent freely from any internet-connected device, SMS travels across a closed network. To gain access, bad actors need expensive hardware or a third-party messaging provider to inject messages into the network for them.
The role of mobile messaging providers
In this follow up, we’re focusing on the latter method. Messaging providers and aggregators offer a scalable way for businesses to send out mobile messages. And they have plenty of legitimate uses. SMS flight updates, appointment reminders and bank notifications are all sent this way. But since these providers typically offer easier access to mobile networks, they have become a popular target for abuse.
Many messaging platforms operate on a freemium model with little user verification. Some even allow people to register with just a prepaid “burner” number. So even if abuse is detected from one device, cyber criminals can register a new one—or hundreds of them. There have also been reports of bad actors using fake or stolen credit card numbers. Some even access these platforms with stolen credentials.
How cyber criminals abuse these services
Another advantage these services offer is access to high-value mobile markets like the U.S. and U.K. Looking at the point of origin for smishing messages delivered by a popular U.S.-based platform shows messages being sent from across the globe. For a cyber criminal in Pakistan or Cambodia to send SMS to the U.S. directly would be prohibitively expensive. However, with free options available, these attackers could pay nothing to target U.S. consumers.
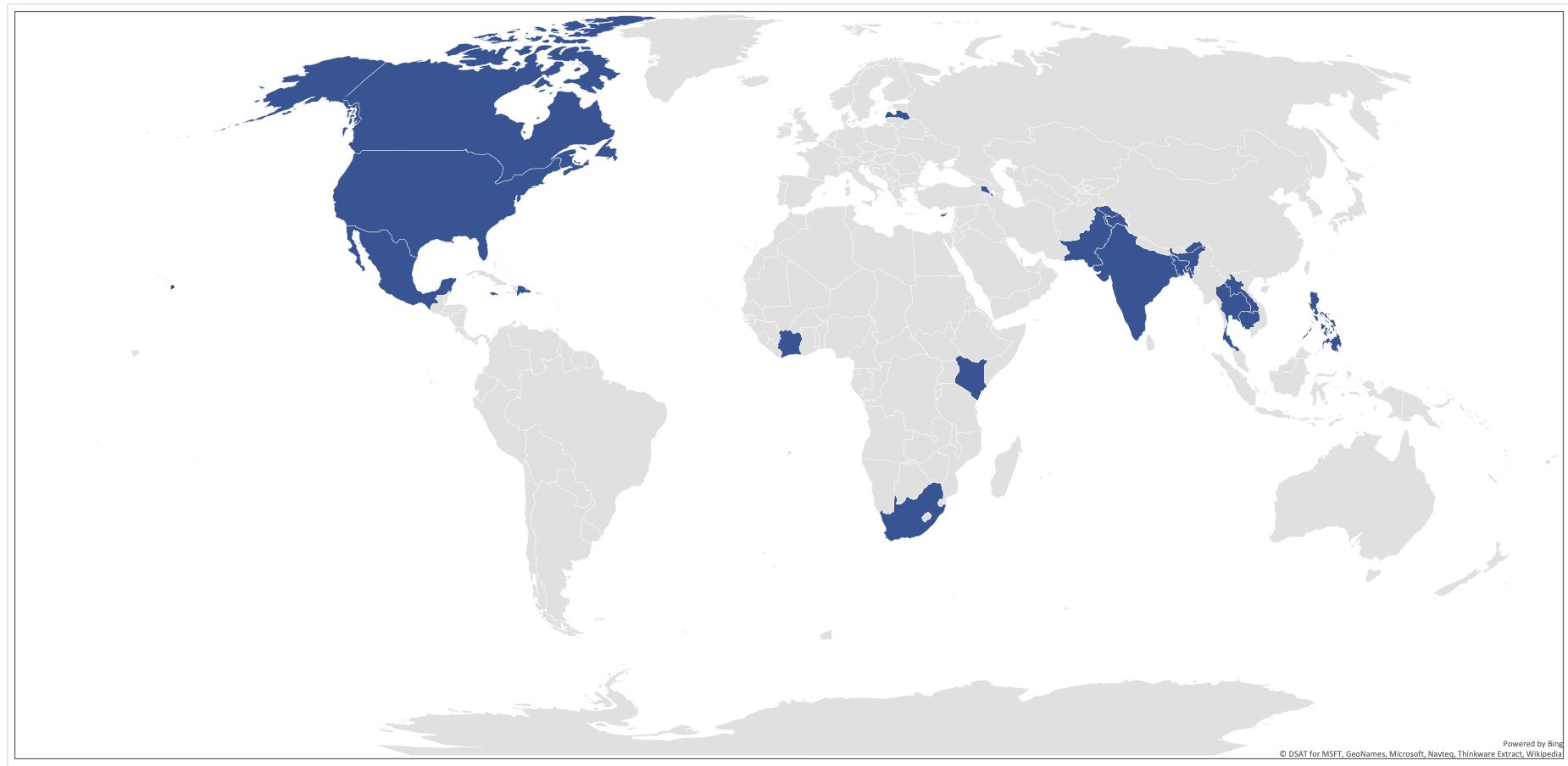
Figure 1. Top-20 originating countries by reported smishing volume from one U.S.-based message platform
Many cyber criminals use message platforms to initiate conversational attacks. These usually start with an innocuous message—often just a simple, “Hey, how are you?” To establish rapport, multiple messages may need to be sent. These attacks are often multimodal and can move away from SMS to a messaging service like WhatsApp. They may also ask victims to invest money on fake cryptocurrency platforms or other fraudulent financial sites.
Another common attack involves spoofing legitimate message types, such as delivery notifications or password resets. These messages can lead to smishing sites, or less commonly, to malware delivery.
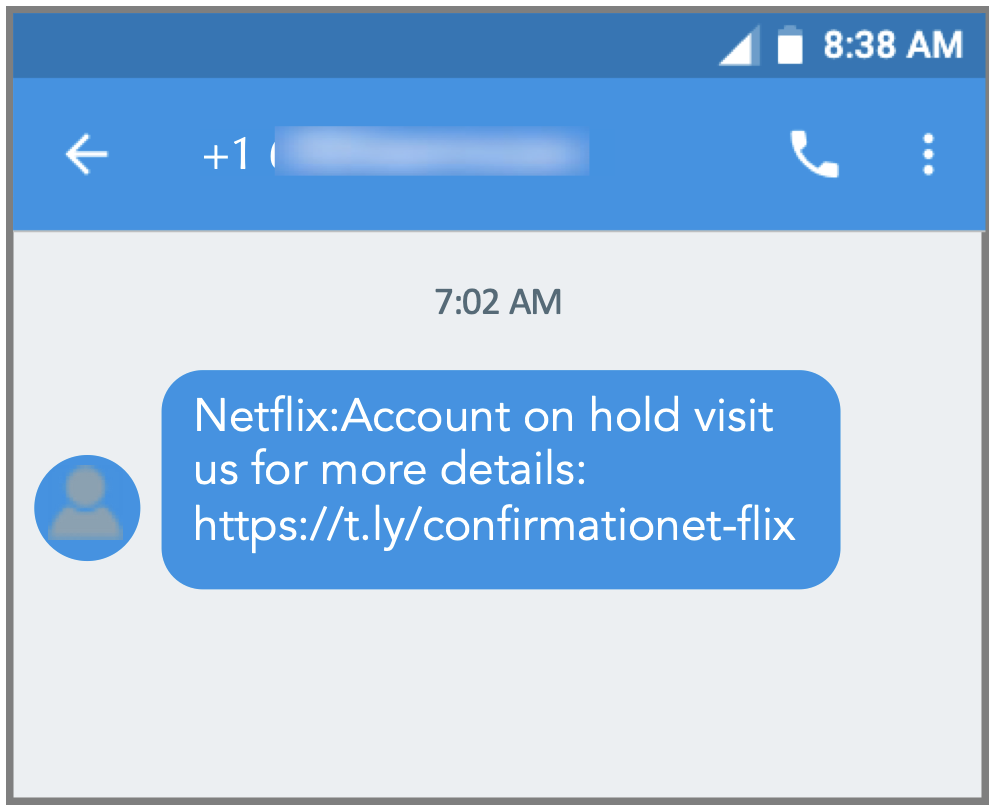
Figure 2. A typical Netflix-themed malicious SMS
Finally, in addition to overt threats, messaging platforms are also abused to deliver spam. This can take the form of political messaging, local offers, or alerts for social campaigns. Most of the time these texts don’t respect opt-in/opt-out settings or allow users to request removal.
How mobile messaging providers can fight back
Without messaging providers lowering barriers to entry, bad actors would have to make a serious financial investment to access mobile networks. Smishing is a hard problem; malicious messages are often indistinguishable from legitimate updates and notifications. But solving it is critical to maintaining trust in mobile.
Mobile network operators already filter messages to protect users from malicious SMS. These same technologies can be installed by messaging providers to detect smishing before messages are even transmitted to the networks. Removing malicious messages before they are sent should decrease costs for these providers, since they typically pay for every message, they inject into the network. More important, it will help maintain the integrity of mobile communications on which these businesses and so many others depend.
Check out the Threat Hub for more great insights.
